Trust me, we are Batmen and we are saving your assets from prying eyes.
Just like Batman protects Gotham City, safeguarding your personal data from various threats is crucial. In this blog post, we'll explore the concept of threat modeling and how it can help you fortify your personal security posture. By understanding and applying these principles, you'll be better equipped to defend your valuable assets from potential adversaries.
Threat Modeling
With the attacks on privacy everywhere in the world, from mass surveillance to anti-privacy laws, threats to our personal security and privacy are more prevalent than ever.
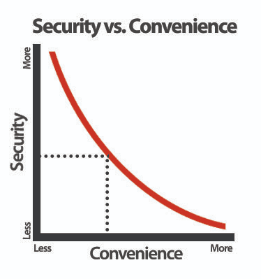
Threat modeling empowers you to take a proactive approach to your personal security posture, rather than simply reacting to threats as they come. It's crucial to acknowledge the trade-off between convenience and security. Implementing stringent security measures can sometimes come at the cost of usability and ease of access. Threat modeling helps you strike the right balance by focusing on the most probable and impactful threats while maintaining a level of convenience that works for you. By understanding your unique threat landscape, you can make informed decisions about where to invest your time and effort to secure your assets.
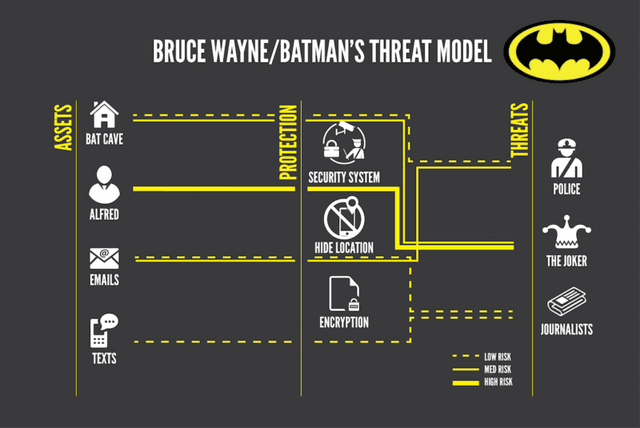
Understanding Assets
First, identify your critical assets – the things you want to protect. These could be:
- Your devices (like Batman's Bat Cave)
- Personal information
- Important files
- Online accounts
Make a list of these assets and prioritize them based on their importance and sensitivity.
Identifying Threats
Next, consider the threats that could compromise your assets. These threats can come from various sources, such as:
- Cybercriminals
- Hackers
- Nosy journalists (as depicted in Batman's threat model)
Common threats include:
- Malware
- Phishing attempts
- Unauthorized access
- Data breaches
- Big tech spying on your personal data
Assessing Risks
Now, evaluate the likelihood and potential impact of each threat. Assign a risk level to each threat based on how likely it is to occur and how severe the consequences would be. This will help you prioritize your security measures and focus on the most significant risks.
Mitigating Risks
Once you've identified and assessed the risks, it's time to implement security controls to mitigate them. This can include measures like:
- Using strong passwords
- Enabling two-factor authentication
- Encrypting sensitive data (just like Batman's encryption)
- Regularly updating your software and devices
- Using privacy-enhancing tools and techniques to protect your online activities and hide your location (like Batman's hide location)
Continuous Improvement
Threat modeling is an ongoing process. As new threats emerge and your personal circumstances change, it's essential to regularly review and update your threat model. Stay informed about the latest security best practices and be proactive in adapting your defenses.
Remember, just like Batman, vigilance and continuous improvement are key to staying one step ahead of potential threats.
Start your threat modeling journey today and create a personal security strategy that even the Dark Knight would be proud of!
Resources
- EFF Surveillance Self-Defense Guide
- OWASP Threat Modeling
- Privacy Guides Online Learning - Basics of Personal Threat Modeling
Let's work together to create a safer world for everyone!